Stealing data with physical attacks
When it comes to data privacy, current technologies can protect data while in transit and at rest. However, attackers with physical access to servers may extract sensitive data while in use and completely bypass traditional in-transit and at-rest controls.
Credit card numbers, bank account numbers, secret keys, or personal data may all reside in memory and be vulnerable to these types of attacks. Contrary to popular belief, attacks to extract the state of a running server do not require high skill levels or sophisticated attack tools. Example attack case studies illustrate the risk of physical attacks in the real world.
Accessing vulnerable server memory
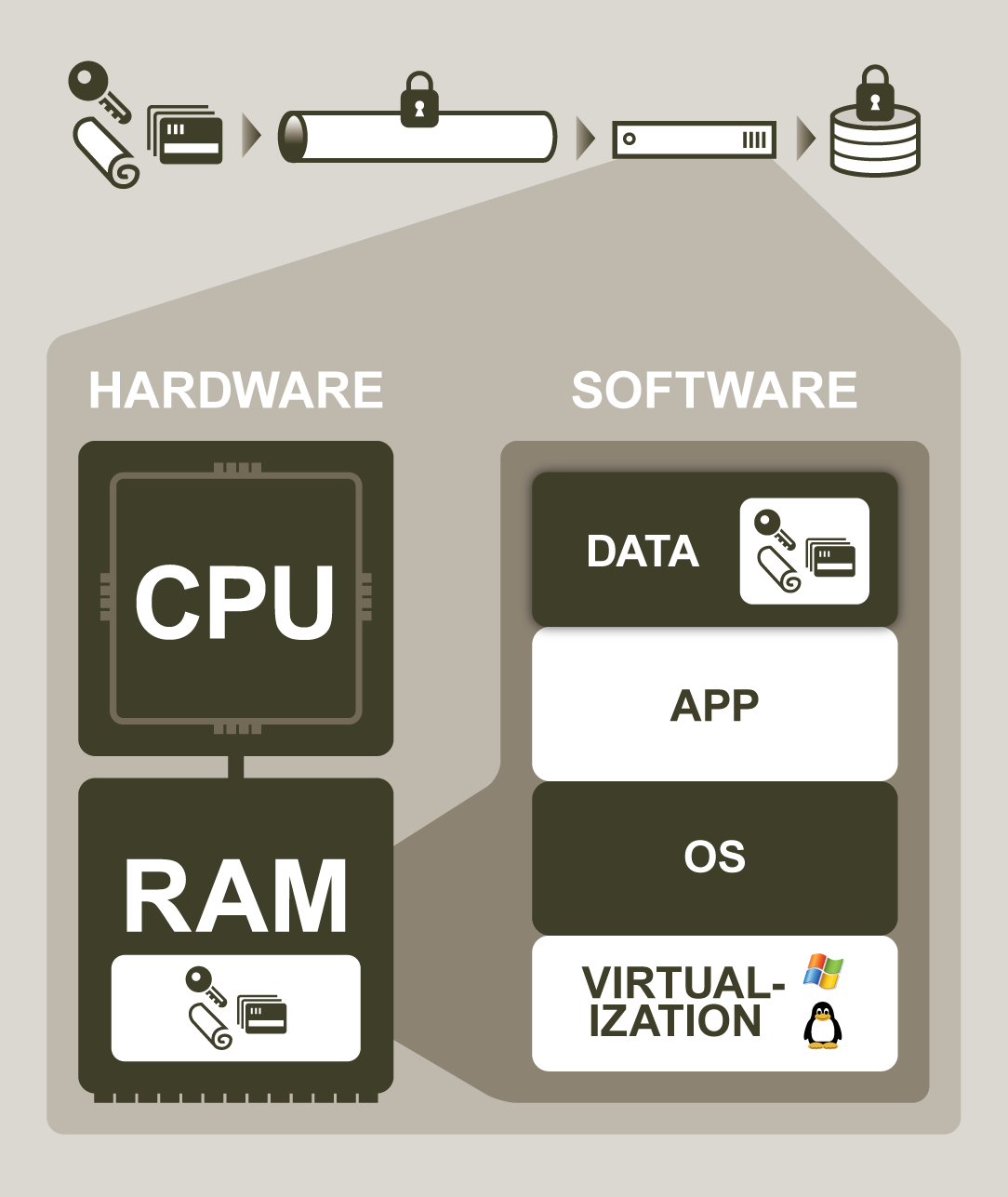
On many system configurations, it is simple to conduct a reset attack, which entails rebooting a server into a malicious operating system (OS), then dumping any memory state left behind by the previously-running software stack. In many cases, this attack may be carried out using an ordinary USB storage device containing the malicious OS and space to copy memory contents.
Two example tools to capture memory from a bootable USB are Princeton’s bios_memimage and McGrew Security’s msramdmp. For some servers supporting remote KVM (Keyboard-Video-Mouse) with virtual media, reset attacks may be executed over the network without having physical access to the server.
Another straight-forward way to steal sensitive data is to simply remove a memory card from the server, then read its contents from another computer. Surprisingly, standard DRAM memory modules found in most laptops and servers may retain data contents for several seconds, and if cooled, for several minutes. This allows ample time for an attacker to extract data from the memory card. Researchers from Princeton University published details of using this “cold boot” attack to successfully steal secret data.
Yet another attack vector to access server memory is via programmable input/output (I/O) devices. Malicious I/O devices installed on a system can use an access method known as direct memory access, or DMA, to read from or write to main memory. Memory-stealing DMA attacks may be conducted by corrupted off-the-shelf devices like network cards, which can transmit stolen data over a network. DMA attacks may also be conducted through external interfaces like FireWire or Thunderbolt.
Even memory modules themselves may be a hidden risk. Widely available non-volatile RAM (NVRAM) are designed to persist memory contents for long periods of time and can be easily recovered by an attacker. Malicious memory modules, which alter the contents of memory to invisibly compromise a system, are also a growing threat. Former CIA and NSA chief Gen. Michael Hayden called these types of sabotaged devices the “problem from hell”.
Defending from physical attacks
PrivateCore is developing software-based defenses to these types of physical attacks. Our solution runs on commodity x86 hardware and does not require any changes to existing virtual machines or applications. Contact us to learn more about protecting your organization’s servers from physical attacks.